宝塔面板下站点如何只限定CDN的IP节点回源请求。
- 服务器知识
- 2023-09-06
- 44热度
- 0评论
现在很多站长都知道给自己站点套个CDN 是越来越有必要了,毕竟现在 DDos/CC 攻击实在是太泛滥了,借助CDN 能给站点加速的同时,还可以很好的隐藏服务器真实IP,如果能利用好CDN 的WAF更是能很好的提升网站安全防御能力,再如果接入免费CloudFlare的话,让你的网站成为打不死的小强都不是梦。
要想让CDN 更好的发挥作用提升安全性,就得利用好CDN 的IP节点回源请求了,让所有访问请求都通过CDN 节点IP来回源请求目前是个很好的办法,但是对于使用宝塔面板的还是不太友好和方便,今天明月就给大家分享一下宝塔面板下站点如何只限定CDN的IP节点回源请求。
受限于宝塔面板默认防火墙Firewalld的限制,要想宝塔面板下站点如何只限定CDN的IP节点回源请求的话,最简便有效的办法就是将CDN 的IP节点一个一个的加入到宝塔的【端口规则】里,需要限制哪个端口就在哪个端口下添加,如下图:
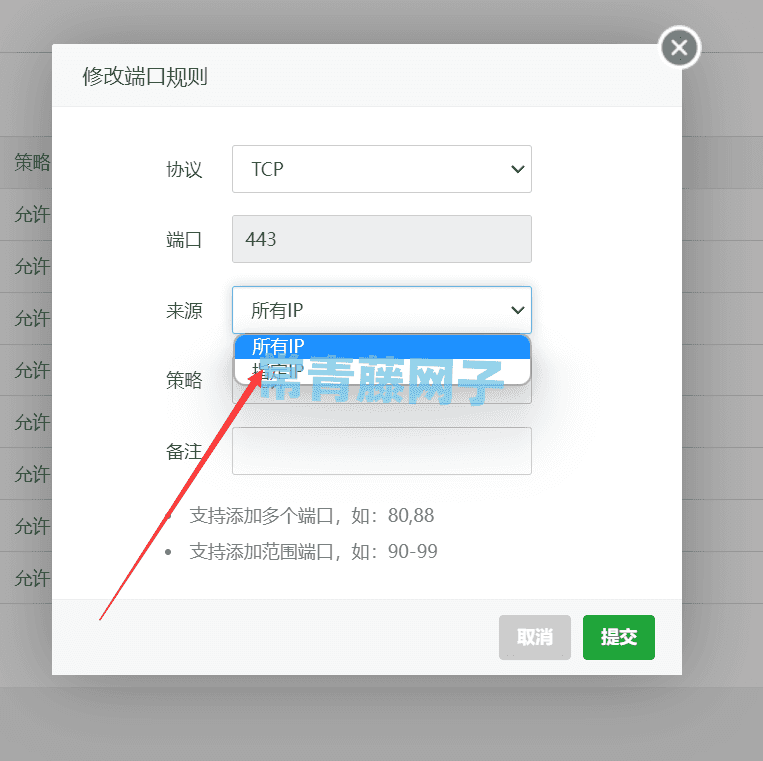
修改**所有IP**为**指定IP**
上图我们选择的是443端口,默认宝塔是开放443端口给所有IP的,所以这里我们必须修改443端口规则为“指定IP”,切记切记哦!
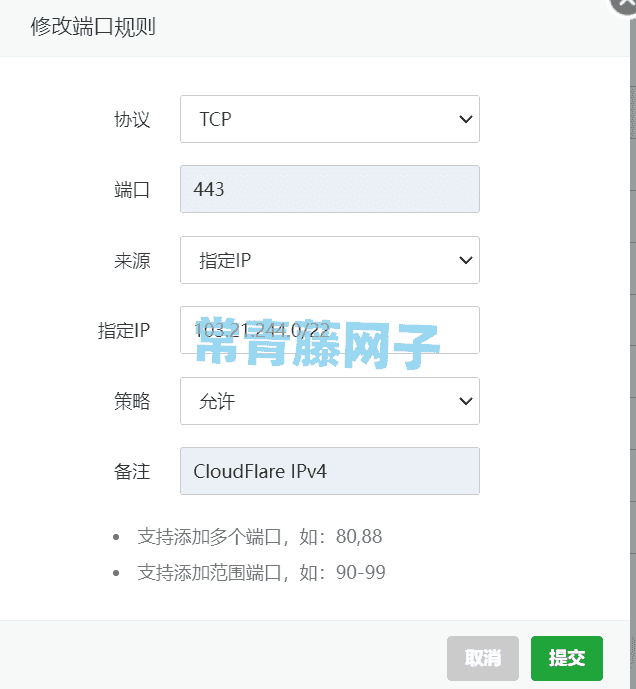
如上图就是给443添加了一个CloudFlare的IPv4节点IP地址段,意思就是这个103.21.244.0/22地址段的IP都可以回源请求443端口。具体CloudFlare的节点IP可以到这里查看:https://www.cloudflare-cn.com/ips/
添加CDN 节点IP地址段
剩下的我们只需要一个一个的把CloudFlare的IPv4节点IP地址段这样添加即可,如果是80端口也是同样的。有人会说这样很麻烦,效率太低不科学,那么我们可以使用宝塔的【导出规则】和【导入规则】来批量的添加,具体步骤很简单,先【导出规则】下载获得一个叫port.json的文件,具体内容如下(仅供参考):
{"id": 8, "protocol": "tcp", "ports": "888", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}
{"id": 7, "protocol": "tcp", "ports": "39000-40000", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}
{"id": 6, "protocol": "tcp", "ports": "33368", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}
{"id": 5, "protocol": "tcp", "ports": "443", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}
{"id": 4, "protocol": "tcp", "ports": "80", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}
{"id": 3, "protocol": "tcp", "ports": "22", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}
{"id": 2, "protocol": "tcp", "ports": "21", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}
{"id": 1, "protocol": "tcp", "ports": "20", "types": "accept", "address": "", "brief": "", "addtime": "2023-05-30 21:06:40"}参考这个导出规则,我们可以制作一个导入CloudFlare的IP节点的.json,具体内容如下参考:
{"id": 24, "protocol": "tcp", "ports": "443", "types": "accept", "address": "198.41.128.0/17", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 23, "protocol": "tcp", "ports": "443", "types": "accept", "address": "197.234.240.0/22", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 22, "protocol": "tcp", "ports": "443", "types": "accept", "address": "190.93.240.0/20", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 21, "protocol": "tcp", "ports": "443", "types": "accept", "address": "188.114.96.0/20", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 21, "protocol": "tcp", "ports": "443", "types": "accept", "address": "173.245.48.0/20", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 19, "protocol": "tcp", "ports": "443", "types": "accept", "address": "172.64.0.0/13", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 18, "protocol": "tcp", "ports": "443", "types": "accept", "address": "162.158.0.0/15", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 17, "protocol": "tcp", "ports": "443", "types": "accept", "address": "141.101.64.0/18", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 16, "protocol": "tcp", "ports": "443", "types": "accept", "address": "131.0.72.0/22", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 15, "protocol": "tcp", "ports": "443", "types": "accept", "address": "108.162.192.0/18", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 14, "protocol": "tcp", "ports": "443", "types": "accept", "address": "104.16.0.0/13", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 13, "protocol": "tcp", "ports": "443", "types": "accept", "address": "103.31.4.0/22", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 12, "protocol": "tcp", "ports": "443", "types": "accept", "address": "36.170.50.26", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 11, "protocol": "tcp", "ports": "443", "types": "accept", "address": "103.22.200.0/22", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 10, "protocol": "tcp", "ports": "443", "types": "accept", "address": "103.21.244.0/22", "brief": "", "addtime": "2023-05-30 16:40:26"}
{"id": 9, "protocol": "tcp", "ports": "443", "types": "accept", "address": "103.21.244.0/22", "brief": "", "addtime": "2023-05-30 16:40:26"}
这个方法最高效,但需要你非常的细心参考默认导出的规则根据实际来制作,建议大家借助纯文本编辑器EditPlus等在本地编辑好检查无误后再在宝塔面板里【导入规则】即可。
唯一的瑕疵就是需要在每个端口上都这样添加才能实现只限定CDN的IP节点请求这个端口,没办法宝塔这方面没有很便捷的方法了,另外就是这样操作后你在哪个端口限制了,其他IP请求都会被拒绝的,所以一定要仔细核对IP地址段,如果是80端口的还要考虑自己IP的请求哦,别弄完把自己都给屏蔽了,至于自己IP地址段的获取,可以在ipip.net上查询到的,记住是IP地址段,可不是单独一个IP哦!
本文转自明月登楼的博客